10 malicious Python packages exposed in latest repository attack

Researchers have discovered yet another set of malicious packages in PyPi, the official and most popular repository for Python programs and code libraries. Those duped by the seemingly familiar packages could be subject to malware downloads or theft of user credentials and passwords.
Check Point Research, which reported its findings Monday, wrote that it didn’t know how many people had downloaded the 10 packages, but it noted that PyPi has 613,000 active users, and its code is used in more than 390,000 projects. Installing from PyPi through the pip command is a foundational step for starting or setting up many Python projects. PePy, a site that estimates Python project downloads, suggests most of the malicious packages saw hundreds of downloads.
Such supply-chain attacks are becoming increasingly common, especially among open source software repositories that support a wide swath of the world’s software. Python’s repository is a frequent target, with researchers finding malicious packages in September 2017; June, July, and November 2021; and June of this year. But trick packages have also been found in RubyGems in 2020, NPM in December 2021, and many more open source repositories.
Most notably, a private-source supply-chain attack by Russian hackers through the SolarWinds business software wreaked notable havoc, resulting in the infection of more than 100 companies and at least nine US federal agencies, including the National Nuclear Security Administration, the Internal Revenue Service, the State Department, and the Department of Homeland Security.
The increasingly common discovery of fake, malicious packages is moving repositories to act. Just yesterday, GitHub, owner of the NPM repository for JavaScript packages, opened a request for comments on offering an opt-in system for package developers to sign and verify their packages. Using Sigstore, a collaboration among numerous open source and industry groups, NPM developers can sign off on packages, signaling that the code inside them matches their original repository.
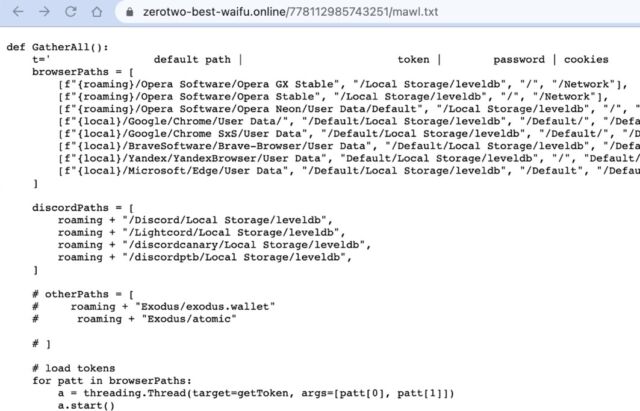
Having a clear indication that the package you’re downloading is related to the code you need might have helped people avoid the most recently discovered PyPi bad actors, though perhaps not entirely. “Ascii2text” directly copied almost every aspect of the ASCII art library “art,” minus the release details. To perhaps nearly 1,000 downloaders, its descriptive name might have suggested a more defined purpose than “art.”
Installing ascii2text triggered the download of a malicious script, which then searched the local storage of Opera, Chrome, and other browsers for tokens, passwords, or cookies, along with certain crypto wallets, and sent them along to a Discord server.
Other packages discovered by Check Point targeted AWS and other credentials and environment variables. Here’s the list of reported and since removed PyPi packages:
- ascii2text
- pyg-utils
- pymocks
- PyProto2
- test-async
- free-net-vpn
- free-net-vpn2
- zlibsrc
- browserdiv
- WINRPCexploit
https://arstechnica.com/?p=1872326