Feel-good story of the week: 2 ransomware gangs meet their demise

From the warm-and-fuzzy files comes this feel-good Friday post, chronicling this week’s takedown of two hated ransomware groups. One vanished on Tuesday, allegedly after being hacked by a group claiming allegiance to Ukraine. The other was taken out a day later thanks to an international police dragnet.
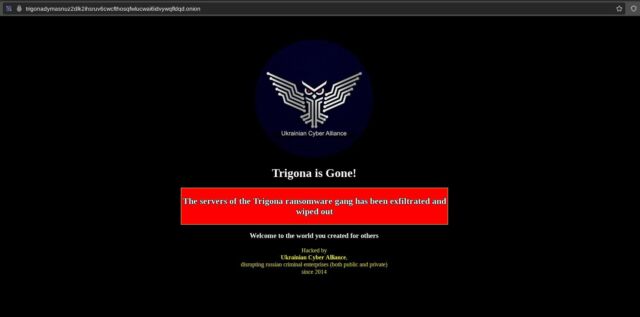
The first group, calling itself Trigona, saw the content on its dark web victim naming-and-shaming site pulled down and replaced with a banner proclaiming: “Trigona is gone! The servers of Trigona ransomware gang has been infiltrated and wiped out.” An outfit calling itself Ukrainian Cyber Alliance took credit and included the tagline: “disrupting Russian criminal enterprises (both public and private) since 2014.”
Poor operational security
A social media post from a user claiming to be a Ukrainian Cyber Alliance press secretary said his group targeted ransomware groups partly because they consider themselves out of reach of Western law enforcement.
“We just found one gang like that and did to them as they do to the rest,” the press secretary wrote. “Downloaded their servers (ten of them), deleted everything and defaced for the last time. TOR didn’t help them or even knowing they had a hole in it. Their entire infrastructure is completely blown away. Such a hunt forward.’”
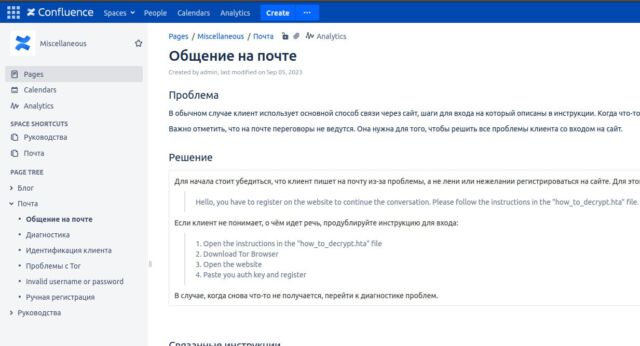
A separate social media post dumped what the press secretary said was an administrative panel key and said the group wiped out Trigona’s “landing, blog, leaks site, internal server (rocketchat, atlassian), wallets and dev servers.” The person also claimed that the Ukrainian Cyber Alliance hacked a Confluence server Trigona used.
By Friday, the Trigona site was unavailable, as evidenced by the message “Onionsite not found.”
Trigona first surfaced in 2022 with close ties to ransomware groups known as CryLock and BlackCat and looser ties to ALPHV. It primarily hacked companies in the US and India, followed by Israel, Turkey, Brazil, and Italy. It was known for compromising MYSQL servers, often by brute forcing passwords. A June profile of the group by researchers from security firm Trend Micro noted that the group’s technical sophistication was mixed.
“The Trigona ransomware group has poor operational security when it comes to the implementation of Tor sites—although their aim of targeting poorly managed SQL servers is not something we usually see with less technically proficient threat actors,” the post stated.
The timeline of the hack, based on the social media posts, suggests that the breach began roughly eight days ago, with the hack of a Confluence server Trigona members used to collaborate. In an interview with the Record, the group said it planned to turn over data it seized to law enforcement authorities.
A takedown 2 years in the making
The second ransomware gang takedown this week happened to Ragnar Locker, a group that has hacked numerous organizations worldwide. On Friday, Europol said:
In an action carried out between 16 and 20 October, searches were conducted in Czechia, Spain and Latvia. The “key target” of this malicious ransomware strain was arrested in Paris, France, on 16 October, and his home in Czechia was searched. Five suspects were interviewed in Spain and Latvia in the following days. At the end of the action week, the main perpetrator, suspected of being a developer of the Ragnar group, has been brought in front of the examining magistrates of the Paris Judicial Court.
The ransomware’s infrastructure was also seized in the Netherlands, Germany and Sweden and the associated data leak website on Tor was taken down in Sweden.
Ragnar Locker emerged in 2019 and quickly became known for its success in hacking organizations in various sectors, including health care, government, technology, finance, education, and media. It’s what’s known as a RAAS (ransomware as a service), in which core members develop the encryption software, run a central server, and then work with affiliates. The affiliates then hack victims, and profits are divided between the two groups. More about the group is available here and here.
Friday’s Europol post said Ragnar Locker members warned victims not to contact authorities because they would only “muck things up.”
In fact, Europol members, along with the FBI and Ukrainian authorities, had been investigating the group since 2021 and steadily made progress, culminating in this week’s arrest and takedown.
“Little did they know that law enforcement was closing in on them,” Europol said.
https://arstechnica.com/?p=1977607