Malicious cheats for Call of Duty: Warzone are circulating online

Criminals have been hiding malware inside publicly available software that purports to be a cheat for Activision’s Call of Duty: Warzone, researchers with the game maker warned earlier this week.
Cheats are programs that tamper with in-game events or player interactions so that users gain an unfair advantage over their opponents. The software typically works by accessing computer memory during gameplay and changing health, ammo, score, lives, inventories, or other information. Cheats are almost always forbidden by game makers.
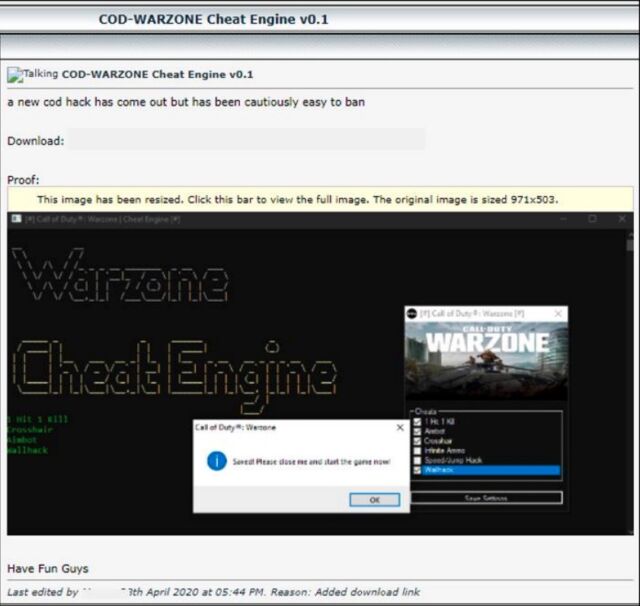
On Wednesday, Activision said that a popular cheating site was circulating a fake cheat for Call of Duty: Warzone that contained a dropper, a term for a type of backdoor that installs specific pieces of malware chosen by the person who created it. Named Warzone Cheat Engine, the cheat was available on the site in April 2020 and again last month.
Shields down
People promoting the cheat instructed users to run the program as an administrator and to disable antivirus. While these settings are often required for a cheat to work, they also make it easier for malware to survive reboots and to go undetected, since users won’t get warnings of the infection or that software is seeking heightened privileges.
“While this method is rather simplistic, it is ultimately a social engineering technique that leverages the willingness of its target (players that want to cheat) to voluntarily lower their security protections and ignore warnings about running potentially malicious software,” Activision researchers wrote in a deep-dive analysis. They provided a long list of Warzone Cheat Engine variants that installed a host of malware, including a cryptojacker, which uses the resources of an infected gaming computer to surreptitiously mine cryptocurrency.
Activision’s analysis said that multiple malware forums have regularly advertised a kit that customizes the fake cheat. The kit makes it easy to create versions of Warzone Cheat Engine that deliver malicious payloads chosen by the criminal using it.
The people selling the kit advertised it as an “effective” way to spread malware and “some nice bait for your first malware project.” The sellers have also posted YouTube videos that promote the kit and explain how to use it.
Activision’s report came on the same day that Cisco’s Talos security team disclosed a new malware campaign targeting gamers who use cheats. The malicious cheats used a previously unknown cryptor tool that prevented antivirus programs from detecting the payload. Talos didn’t identify the game titles that were targeted.
https://arstechnica.com/?p=1754269