Microsoft profiles new threat group with unusual but effective practices

Microsoft has been tracking a threat group that stands out for its ability to cash in from data theft hacks that use broad social engineering attacks, painstaking research, and occasional physical threats.
Unlike many ransomware attack groups, Octo Tempest, as Microsoft has named the group, doesn’t encrypt data after gaining illegal access to it. Instead, the threat actor threatens to share the data publicly unless the victim pays a hefty ransom. To defeat targets’ defenses, the group resorts to a host of techniques, which, besides social engineering, includes SIM swaps, SMS phishing, and live voice calls. Over time, the group has grown increasingly aggressive, at times resorting to threats of physical violence if a target doesn’t comply with instructions to turn over credentials.
“In rare instances, Octo Tempest resorts to fear-mongering tactics, targeting specific individuals through phone calls and texts,” Microsoft researchers wrote in a post on Wednesday. “These actors use personal information, such as home addresses and family names, along with physical threats to coerce victims into sharing credentials for corporate access.”
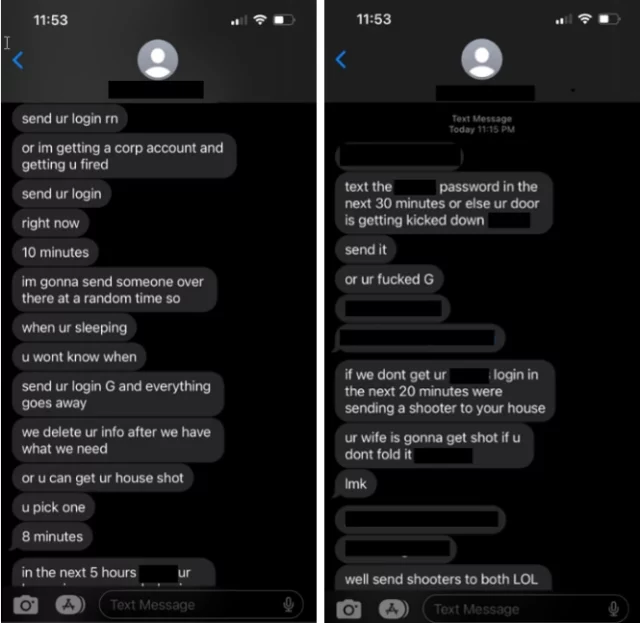
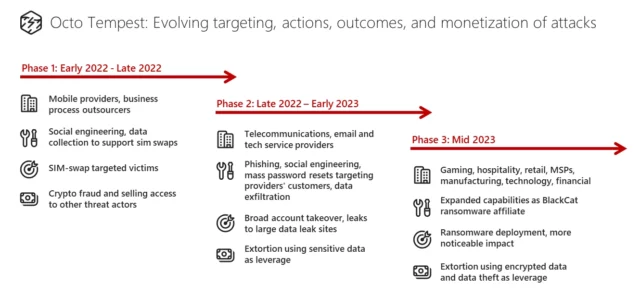
Octo Tempest first came to notice early last year as it used SIM swaps to ensnare companies that provide mobile telecommunications processing services to other companies. The group would then sell the unauthorized access it gained through those swaps to other crime groups or use them to perform account takeovers of high-net-worth individuals to steal their cryptocurrency. By the end of the year, the group had broadened its techniques and expanded its targets to include cable telecommunications, email, and technology organizations. Around this time, it began extorting victims whose data it had stolen, sometimes resorting to physical threats.
Earlier this year, the native-English-speaking group became an affiliate of the ALPHV/BlackCat ransom-as-a-service operation. That made the group stand out since Eastern European ransomware crime syndicates rarely accept English-speaking members. Octo Tempest’s ALPHV/BlackCat ransomware attacks target both Windows and Linux versions systems, often when they run on VMWare ESXi servers. Targets often are in industries including natural resources, gaming, hospitality, consumer products, retail, managed service providers, manufacturing, law, technology, and financial services.
“In recent campaigns, we observed Octo Tempest leverage a diverse array of TTPs to navigate complex hybrid environments, exfiltrate sensitive data, and encrypt data,” Microsoft wrote. “Octo Tempest leverages tradecraft that many organizations don’t have in their typical threat models, such as SMS phishing, SIM swapping, and advanced social engineering techniques.”
The researchers continued:
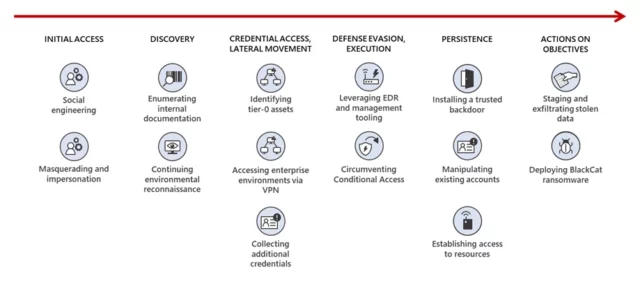
Octo Tempest commonly launches social engineering attacks targeting technical administrators, such as support and help desk personnel, who have permissions that could enable the threat actor to gain initial access to accounts. The threat actor performs research on the organization and identifies targets to effectively impersonate victims, mimicking idiolect on phone calls and understanding personal identifiable information to trick technical administrators into performing password resets and resetting multifactor authentication (MFA) methods. Octo Tempest has also been observed impersonating newly hired employees in these attempts to blend into normal on-hire processes.
Octo Tempest primarily gains initial access to an organization using one of several methods:
- Social engineering
- Calling an employee and socially engineering the user to either:
- Install a Remote Monitoring and Management (RMM) utility
- Navigate to a site configured with a fake login portal using an adversary-in-the-middle toolkit
- Remove their FIDO2 token
- Calling an organization’s help desk and socially engineering the help desk to reset the user’s password and/or change/add a multi-factor authentication token/factor
- Purchasing an employee’s credentials and/or session token(s) on a criminal underground market
- SMS phishing employee phone numbers with a link to a site configured with a fake login portal using an adversary-in-the-middle toolkit
- Using the employee’s pre-existing access to mobile telecommunications and business process outsourcing organizations to initiate a SIM swap or to set up call number forwarding on an employee’s phone number. Octo Tempest will initiate a self-service password reset of the user’s account once they have gained control of the employee’s phone number.
Additional tradecraft includes:
- PingCastle and ADRecon to perform reconnaissance of Active Directory
- Advanced IP Scanner to probe victim networks
- Govmomi Go library to enumerate vCenter APIs
- PureStorage FlashArray PowerShell module to enumerate storage arrays
- AAD bulk downloads of users, groups, and devices.
Microsoft’s post contains various other details, along with defenses organizations can adopt to repel the attacks. Defenses include using out-of-band communications when interacting with co-workers, educating employees, and implementing FIDO-compliant multifactor authentication. https://arstechnica.com/?p=1979474