Threat Actor Abuses SuperMailer for Large-scale Phishing Campaign
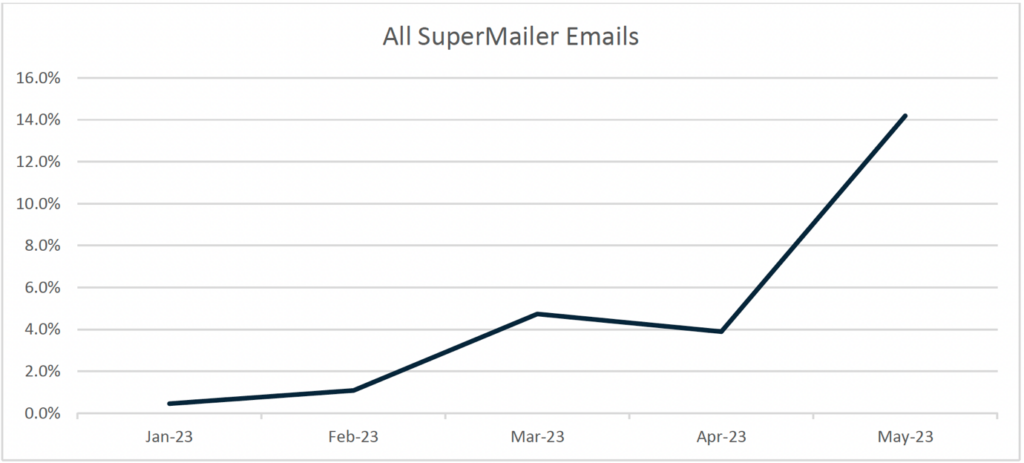
A credential phishing campaign using the legitimate SuperMailer newsletter distribution app has doubled in size each month since January 2023.
“In January this campaign was limited to only a handful of emails, but in May we have seen thousands reaching inboxes,” Brad Haas, cyber threat intelligence analyst at Cofense, told SecurityWeek.
The campaign was discovered courtesy of a unique string included by SuperMailer in an embedded URL within the phishing email. This string is only visible to the email recipient by hovering the cursor over the link – but it shouldn’t have been there. It is the result of a coding error made by the threat actor, but its presence links multiple different phishes to the same campaign.
“The error occurred in a small subset of what has turned into a high-volume credential phishing campaign,” writes Cofense in a report on the campaign. The volume of phishing emails containing this error has continuously increased until, by May 2023, they accounted for 5% of all phishing emails discovered by Cofense.
While analyzing these emails, Cofense discovered other unique identifiers. The firm widened its search to include those additional identifiers, looking for phishes that did not include the error but still reached users’ inboxes. It discovered that by May 15, 2023, a colossal 14% of all phishing emails found since January were part of the same SuperMailer campaign.
The techniques used in this campaign are not new, but the combination is proving successful in getting through technological phishing defenses. These include open redirects, varied senders, URL randomization, and reply chains appended to some of the emails which may make them more likely to pass SEG evaluation or appear legitimate to recipients. Although open redirects are discouraged, they can still be found on even high profile sites – this campaign, for example, used one found on YouTube.
The combination of these techniques with the customization and mass-mailing capabilities of SuperMailer has enabled the phishing emails to reach inboxes protected by a variety of secure email gateways including Proofpoint, Microsoft ATP, Cisco Ironport, Mimecast, Fortinet, and TrendMicro.
The social engineering element of the emails is the tried and tested – and still evidently successful – request for password details.
For now, even large phishing campaigns are still achieved without using the evolving capabilities of artificial intelligence (AI) such as that demonstrated first by ChatGPT. This is probably just a cost/return judgment by the attackers.
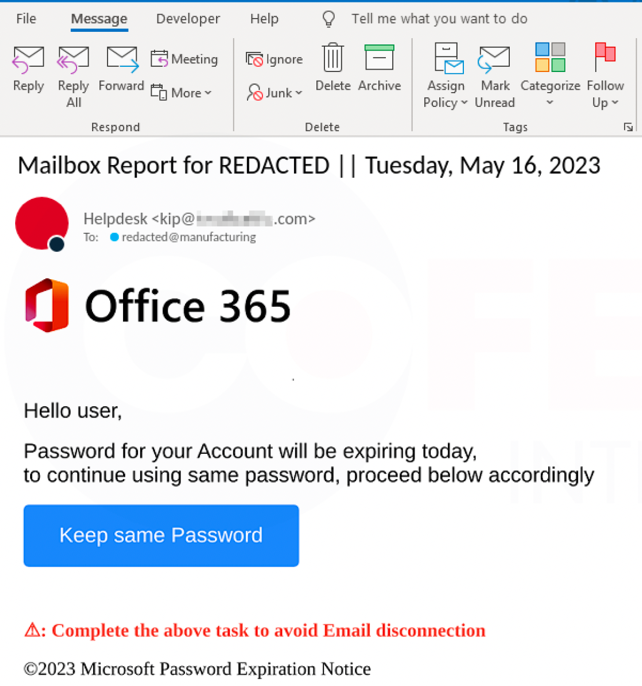
“The threat actors’ current approach is to use very basic content templates and randomization of very small portions of the email,” explains Haas. “They’re casting a wide net by sending so many emails. Adding personalized AI-generated content to each email would involve significant investment of time and resources, and given the current success of the campaign in its effort to reach inboxes, the threat actors would likely not feel a need to change tactics.”
The ’wide net’ cast in this campaign is reaching users in sectors including construction, consumer goods, energy, financial services, food service, government, healthcare, information and analytics, insurance, manufacturing, media, mining, professional services, retail, technology, transportation, and utilities.
The question posed by this campaign, which uses known technology and old social engineering, is how can we detect and prevent phishing.
“Will trained human-beings ever be able to completely defeat phishing/socially engineered attacks? No,” says Haas. “As social engineering tactics become more sophisticated, any well-trained person can still fall for these.”
But there’s scope for partial success. “Can employees who are educated and trained properly see things that intuitively cause them to report a potential threat? Yes,” he continued. “Can the same be said about technology? That depends on the intelligence you are feeding the technology and what it’s trained to detect.”
He concludes, “It is extremely important to have a security solution that makes use of both technology and human intuition. Technology can reduce the load on humans by blocking further instances and variants of what humans have already recognized as a threat. But as threat actors modify their tactics, human training and intuition will always be a critical line of defense.”
The bottom line is that it is a cost/return issue for the attackers. For phishing campaigns such as this, a combination of technology and awareness training may eventually tilt the cost/return in favor of the defenders. History tells us, however, that when defenses improve, attackers become more sophisticated. Waiting in the wings for that time are more sophisticated and better targeted phishing campaigns generated by AI. The war between attackers and defenders never ends – it just changes.
Related: Microsoft: BEC Scammers Use Residential IPs to Evade Detection
Related: New ‘Greatness’ Phishing-as-a-Service Targets Microsoft 365 Accounts
Related: UK Gov Warns of Phishing Attacks Launched by Iranian, Russian Cyberspies
Related: CISA Urges Organizations to Implement Phishing-Resistant MFA
https://www.securityweek.com/threat-actor-abuses-supermailer-for-large-scale-phishing-campaign/