Zyxel Firewalls Hacked by Mirai Botnet
A Mirai botnet variant has been exploiting a recently patched vulnerability tracked as CVE-2023-28771 to hack many Zyxel firewalls.
The Taiwan-based networking device manufacturer informed customers about the security hole on April 25, when it announced the availability of patches for impacted ATP, VPN, USG Flex and ZyWALL/USG firewalls.
The OS command injection vulnerability, found by Trapa Security, is caused by improper error message handling in some firewalls, and it could allow an unauthenticated attacker to remotely execute OS commands by sending specially crafted packets to the targeted device.
By mid-May, security experts reported reproducing the exploit, and Rapid7 warned a few days later that it would likely end up being exploited in the wild.
Rapid7 said it had seen 42,000 instances of internet-exposed Zyxel device web interfaces, but noted that the actual number of exploitable devices was likely much higher.
Researcher Kevin Beaumont reported on Thursday that CVE-2023-28771 has been ‘mass exploited’ by a Mirai botnet variant, with many SMB appliances being impacted.
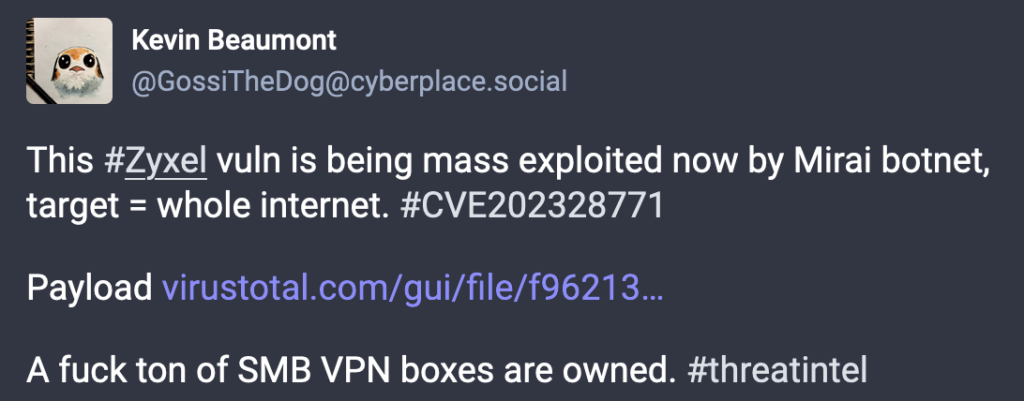
Mirai botnets typically abuse compromised devices to launch DDoS attacks, which can be massive.
It’s not uncommon for hackers to target Zyxel devices using recently patched vulnerabilities.
Zyxel this week announced fixes for two other potentially serious flaws affecting its firewalls. The bugs, tracked as CVE-2023-33009 and CVE-2023-33010, are buffer overflows that can allow unauthenticated attackers to cause a DoS condition or execute arbitrary code on affected devices.
Related: Zyxel Patches Critical Vulnerability in NAS Firmware
Related: Technical Details Released for Recently Patched Zyxel Firewall Vulnerabilities
Related: Critical Vulnerability Allows Remote Hacking of Zyxel Firewalls
https://www.securityweek.com/zyxel-firewalls-hacked-by-mirai-botnet-via-recently-patched-vulnerability/