
Mass exploitation began over the weekend for yet another critical vulnerability in widely used VPN software sold by Ivanti, as hackers already targeting two previous vulnerabilities diversified, researchers said Monday.
The new vulnerability, tracked as CVE-2024-21893, is what’s known as a server-side request forgery. Ivanti disclosed it on January 22, along with a separate vulnerability that so far has shown no signs of being exploited. Last Wednesday, nine days later, Ivanti said CVE-2024-21893 was under active exploitation, aggravating an already chaotic few weeks. All of the vulnerabilities affect Ivanti’s Connect Secure and Policy Secure VPN products.
A tarnished reputation and battered security professionals
The new vulnerability came to light as two other vulnerabilities were already under mass exploitation, mostly by a hacking group researchers have said is backed by the Chinese government. Ivanti provided mitigation guidance for the two vulnerabilities on January 11 and released a proper patch last week. The Cybersecurity and Infrastructure Security Agency, meanwhile, mandated all federal agencies under its authority disconnect Ivanti VPN products from the Internet until they are rebuilt from scratch and running the latest software version.
By Sunday, attacks targeting CVE-2024-21893 had mushroomed, from hitting what Ivanti said was a “small number of customers” to a mass base of users, research from security organization Shadowserver showed. The steep line in the right-most part of the following graph tracks the vulnerability’s meteoric rise starting on Friday. At the time this Ars post went live, the exploitation volume of the vulnerability exceeded that of CVE-2023-46805 and CVE-2024-21887, the previous Ivanti vulnerabilities under active targeting.
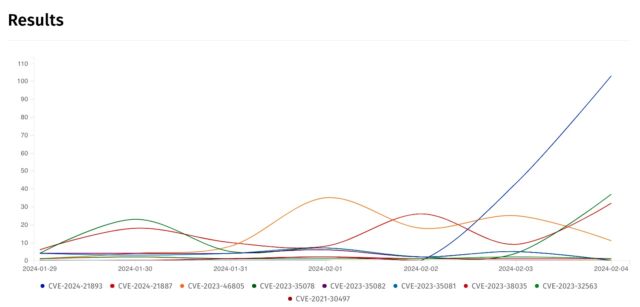
Systems that had been inoculated against the two older vulnerabilities by following Ivanti’s mitigation process remained wide open to the newest vulnerability, a status that likely made it attractive to hackers. There’s something else that makes CVE-2024-21893 attractive to threat actors: because it resides in Ivanti’s implementation of the open source Security Assertion Markup Language—which handles authentication and authorization between parties—people who exploit the bug can bypass normal authentication measures and gain access directly to the administrative controls of the underlying server.
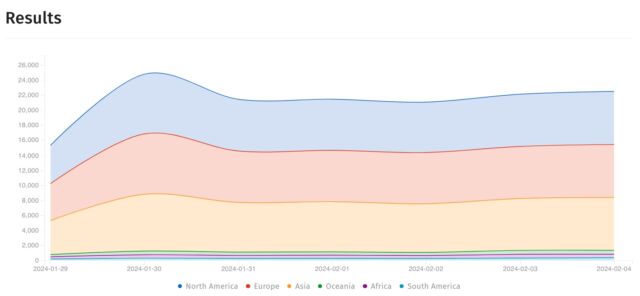
Exploitation likely got a boost from proof-of-concept code released by security firm Rapid7 on Friday, but the exploit wasn’t the sole contributor. Shadowserver said it began seeing working exploits a few hours before the Rapid7 release. All of the different exploits work roughly the same way. Authentication in Ivanti VPNs occurs through the doAuthCheck function in an HTTP web server binary located at /root/home/bin/web. The endpoint /dana-ws/saml20.ws doesn’t require authentication. As this Ars post was going live, Shadowserver counted a little more than 22,000 instances of Connect Secure and Policy Secure.
VPNs are an ideal target for hackers seeking access deep inside a network. The devices, which allow employees to log in to work portals using an encrypted connection, sit at the very edge of the network, where they respond to requests from any device that knows the correct port configuration. Once attackers establish a beachhead on a VPN, they can often pivot to more sensitive parts of a network.
The three-week spree of non-stop exploitation has tarnished Ivanti’s reputation for security and battered security professionals as they have scrambled—often in vain—to stanch the flow of compromises. Compounding the problem was a slow patch time that missed Ivanti’s own January 24 deadline by a week. Making matters worse still: hackers figured out how to bypass the mitigation advice Ivanti provided for the first pair of vulnerabilities.
Given the false starts and high stakes, CISA’s Friday mandate of rebuilding all servers from scratch once they have installed the latest patch is prudent. The requirement doesn’t apply to non-government agencies, but given the chaos and difficulty securing the Ivanti VPNs in recent weeks, it’s a common-sense move that all users should have taken by now.
https://arstechnica.com/?p=2001230

