
A fast-moving botnet that appeared over the weekend has already infected thousands of Android devices with potentially destructive malware that mines digital coins on behalf of the unknown attackers, researchers said.
The previously unseen malware driving the botnet has worm-like capabilities that allow it to spread with little or no user interaction required, researchers with Chinese security firm Netlab wrote in a blog post published Sunday. Once infected, Android phones and TV boxes scan networks for other devices that have Internet port 5555 open. Port 5555 is normally closed, but a developer tool known as the Android Debug Bridge opens the port to perform a series of diagnostic tests. Netlab’s laboratory was scanned by infected devices from 2,750 unique IPs in the first 24 hours the botnet became active, a figure that led researchers to conclude that the malware is extremely fast moving.
“Overall, we think there is a new and active worm targeting Android systems’ ADB debug interface spreading, and this worm has probably infected more than 5,000 devices in just 24 hours,” Netlab researchers wrote. “Those infected devices are actively trying to spread malicious code.”
The researchers said they were withholding some information about the devices that are getting infected, presumably to make it harder for copycat attackers to exploit the same underlying weakness or vulnerability.
Once infected, devices are saddled with an app that causes them to mine the digital coin known as Monero. It’s not clear what precise effect this mining has on the devices. In past cases, however, Monero mining apps are so aggressive they physically damage the Android devices running them.
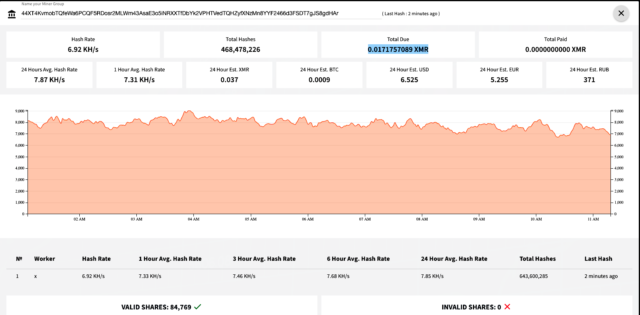
Information returned by Monero Hash Vault—the mining pool the malicious apps use to generate the digital coin—showed the attackers have a 24-hour average rate of 7,880 hashes per second. That’s a relatively small amount. So far, the attackers have generated 0.0171757089 XMR, which at current prices is worth about $3.
It’s not yet clear precisely how devices are getting infected. As noted earlier, Netlab researchers are withholding some details, but they did provide one potential clue when they said some of the infection code relies on Mirai, the malware that compromises routers and other Internet-of-Things devices by guessing default administrator passwords.
https://arstechnica.com/?p=1254677

