Researchers have discovered malware so stealthy it remained hidden for six years despite infecting at least 100 computers worldwide.
Slingshot—which gets its name from text found inside some of the recovered malware samples—is among the most advanced attack platforms ever discovered, which means it was likely developed on behalf of a well-resourced country, researchers with Moscow-based Kaspersky Lab reported Friday. The sophistication of the malware rivals that of Regin—the advanced backdoor that infected Belgian telecom Belgacom and other high-profile targets for years—and Project Sauron, a separate piece of malware suspected of being developed by a nation-state that also remained hidden for years.
Complex ecosystem
“The discovery of Slingshot reveals another complex ecosystem where multiple components work together in order to provide a very flexible and well-oiled cyber-espionage platform,” Kaspersky Lab researchers wrote in a 25-page report published Friday. “The malware is highly advanced, solving all sorts of problems from a technical perspective and often in a very elegant way, combining older and newer components in a thoroughly thought-through, long-term operation, something to expect from a top-notch well-resourced actor.”
The researchers still don’t know precisely how Slingshot initially infected all its targets. In several cases, however, Slingshot operators got access to routers made by Latvian manufacturer MikroTik and planted a malicious code in it. Specifics of the router technique still aren’t known, but they involve using the a MikroTik configuration utility called Winbox to download dynamic link library files from the router’s file system. One of the files, ipv4.dll, is a malicious download agent created by the Slingshot developers. Winbox transfers ipv4.dll to the target’s computer, loads it into memory, and executes it.
In Slingshot FAQ, the researchers wrote:
This DLL then connects to a hardcoded IP and port (in every cases we saw it was the router’s IP address), downloads the other malicious components, and runs them.
To run its code in kernel mode in the most recent versions of operating systems that have Driver Signature Enforcement, Slingshot loads signed vulnerable drivers and runs its own code through their vulnerabilities.
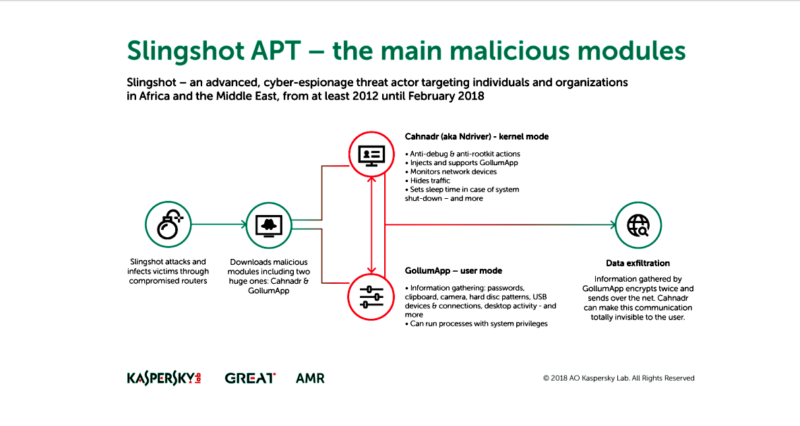
Following infection, Slingshot would load a number of modules onto the victim device, including two huge and powerful ones: Cahnadr, the kernel-mode module, and GollumApp, a user-mode module. The two modules are connected and able to support each other in information gathering, persistence, and data exfiltration.
The most sophisticated module is GollumApp. This contains nearly 1,500 user-code functions and provides most of the above described routines for persistence, file system control, and C&C communications.
Canhadr, also known as NDriver, contains low-level routines for network, IO operations, and so on. Its kernel-mode program is able to execute malicious code without crashing the whole file system or causing Blue Screen—a remarkable achievement. Written in pure C language, Canhadr/Ndriver provides full access to the hard drive and operating memory despite device security restrictions, and [it] carries out integrity control of various system components to avoid debugging and security detection.
The researchers said Slingshot may have used other methods, including zero-day vulnerabilities, to spread. It has been active since at least 2012 and remained operational through last month. The ability for such a fully featured piece of malware to remain hidden for so long is one of the things that makes it so advanced.
One of the ways Slingshot concealed itself was its use of an encrypted virtual file system that was typically located in an unused part of the hard drive. By segregating malware files from the file system of the infected computer, Slingshot stood a much better chance of remaining undetected by antivirus engines. Other stealth techniques included encrypting all text strings in its various modules, calling system services directly to bypass so-called hooks used by security products, and the ability to shut down components when forensic tools are loaded.
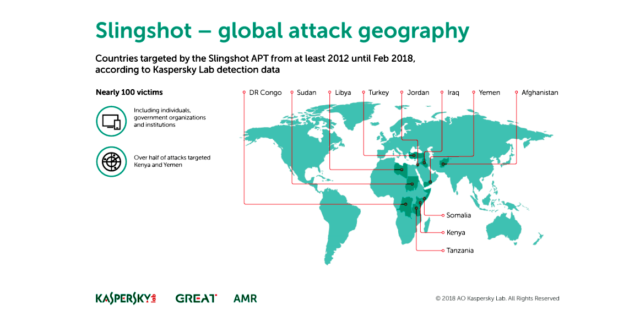
The main purpose of the malware appears to be espionage. Kaspersky Lab’s analysis suggested Slingshot was used to log desktop activity and clipboard contents and to collect screenshots, keyboard data, network data, passwords, and USB connection data. The ability for Slingshot to access the operating system kernel means the malware had access to whatever data was stored on the hard drive or in the internal memory of an infected machine. Infected computers were located primarily in Kenya and Yemen, but also in Afghanistan, Libya, Congo, Jordan, Turkey, Iraq, Sudan, Somalia, and Tanzania. Most of the victims appeared to be targeted individuals. Some, however, were government organizations and institutions.
Debug messages written in perfect English suggest that the developers spoke that language. As is typical for Kaspersky Lab reports, Friday’s report didn’t attempt to identify the developers of Slingshot, other than to say they most likely worked on behalf of a nation-state.
“Slingshot is very complex, and the developers behind it have clearly spent a great deal of time and money on its creation,” company researchers wrote. “Its infection vector is remarkable—and, to the best of our knowledge, unique.”
https://arstechnica.com/?p=1273197

