
Mac malware known as UpdateAgent has been spreading for more than a year, and it is growing increasingly malevolent as its developers add new bells and whistles. The additions include the pushing of an aggressive second-stage adware payload that installs a persistent backdoor on infected Macs.
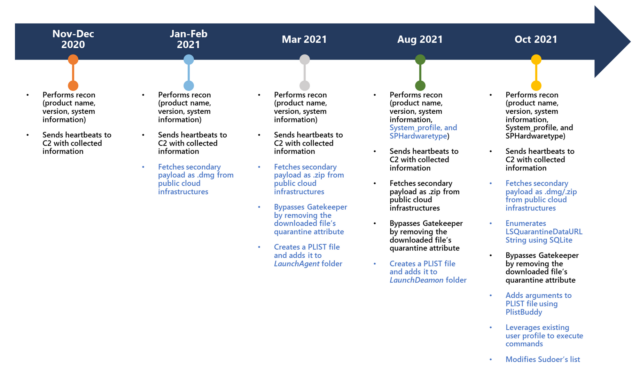
The UpdateAgent malware family began circulating no later than November or December 2020 as a relatively basic information-stealer. It collected product names, version numbers, and other basic system information. Its methods of persistence—that is, the ability to run each time a Mac boots—were also fairly rudimentary.
Person-in-The-Middle attack
Over time, Microsoft said on Wednesday, UpdateAgent has grown increasingly advanced. Besides the data sent to the attacker server, the app also sends “heartbeats” that let attackers know if the malware is still running. It also installs adware known as Adload.
Microsoft researchers wrote:
Once adware is installed, it uses ad injection software and techniques to intercept a device’s online communications and redirect users’ traffic through the adware operators’ servers, injecting advertisements and promotions into webpages and search results. More specifically, Adload leverages a Person-in-The-Middle (PiTM) attack by installing a web proxy to hijack search engine results and inject advertisements into webpages, thereby siphoning ad revenue from official website holders to the adware operators.
Adload is also an unusually persistent strain of adware. It is capable of opening a backdoor to download and install other adware and payloads in addition to harvesting system information that is sent to the attackers’ C2 servers. Considering both UpdateAgent and Adload have the ability to install additional payloads, attackers can leverage either or both of these vectors to potentially deliver more dangerous threats to target systems in future campaigns.
Before installing the adware, UpdateAgent now removes a flag that a macOS security mechanism called Gatekeeper adds to downloaded files. (Gatekeeper ensures users receive a warning that new software comes from the Internet, and it also ensures the software doesn’t match known malware strains.) While this malicious capability isn’t novel—Mac malware from 2017 did the same thing—its incorporation into UpdateAgent indicates the malware is under regular development.
UpdateAgent’s reconnaissance has been expanded to collect system profile and SPHardwaretype data, which, among other things, reveals a Mac’s serial number. The malware also started modifying the LaunchDaemon folder instead of the LaunchAgent folder as before. While the change requires UpdateAgent to run as administrator, the change allows the trojan to inject persistent code that runs as root.
The following timeline illustrates the evolution.
Once installed, the malware collects the system info and sends it to the attackers’ control server and takes a host of other actions. The attack chain of the latest exploit looks like this:
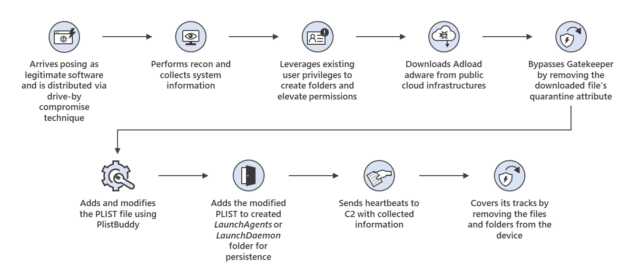
Microsoft said UpdateAgent masquerades as legitimate software, such as video apps or support agents, that is spread through pop-ups or ads on hacked or malicious websites. Microsoft didn’t explicitly say so, but users apparently must be tricked into installing UpdateAgent, and during that process, Gatekeeper works as designed.
In many ways, the evolution of UpdateAgent is a microcosm for the macOS malware landscape as a whole: malware continues to become more advanced. Mac users should learn how to spot social engineering lures, such as unsolicited pop-ups appearing in browser windows that warn of infections or unpatched software.
https://arstechnica.com/?p=1831397

