Meltdown and Spectre are not the only security problems Intel is facing these days. Today, researchers at F-Secure have revealed another weakness in Intel’s management firmware that could allow an attacker with brief physical access to PCs to gain persistent remote access to the system, thanks to weak security in Intel’s Active Management Technology (AMT) firmware—remote “out of band” device management technology installed on 100 million systems over the last decade, according to Intel.
Intel had already found other problems with AMT, announcing last May there was a flaw in some versions of the firmware that could “allow an unprivileged attacker to gain control of the manageability features provided by these products.” Then in November of 2017, Intel pushed urgent security patches to PC vendors for additional management firmware vulnerable to such attacks—technologies embedded in most Intel-based PCs shipped since 2015.
But the latest vulnerability—discovered in July of 2017 by F-Secure security consultant Harry Sintonen and revealed by the company today in a blog post—is more of a feature than a bug. Notebook and desktop PCs with Intel AMT can be compromised in moments by someone with physical access to the computer—even bypassing BIOS passwords, Trusted Platform Module personal identification numbers, and Bitlocker disk encryption passwords—by rebooting the computer, entering its BIOS boot menu, and selecting configuration for Intel’s Management Engine BIOS Extension (MEBx).
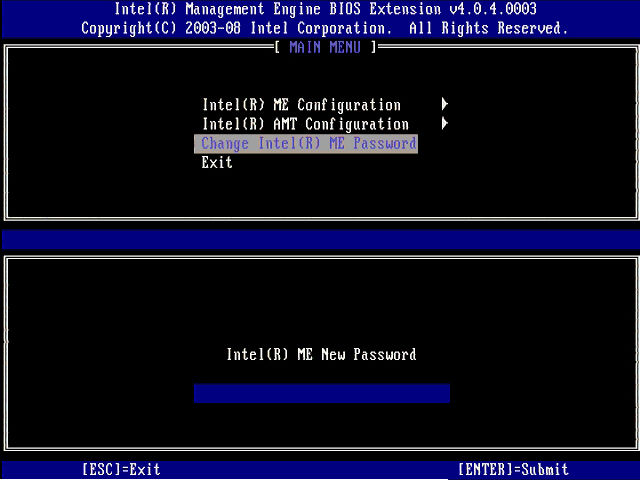
If MEBx hasn’t been configured by the user or by their organization’s IT department, the attacker can log into the configuration settings using Intel’s default password of “admin.” The attacker can then change the password, enable remote access, and set the firmware to not give the computer’s user an “opt-in” message at boot time. “Now the attacker can gain access to the system remotely,” F-Secure’s release noted, “as long as they’re able to insert themselves onto the same network segment with the victim (enabling wireless access requires a few extra steps).”
The attack requires physical access. But the amount of time required to execute the attack is so short that even a notebook or desktop computer left unattended for a few minutes could be compromised in what is referred to by security researchers as an “evil maid” attack—or in this case, an evil barista, co-worker, fellow airline or train passenger, or anyone else with a few minutes of unhindered access to the computer. The remote access is limited to whatever network the targeted computer connects to, but that can include wireless networks.
Late last month, Intel issued guidelines on best practices for configuring AMT to prevent these and other types of AMT-based attacks on PCs. In the “Q&A” document, Intel acknowledged the problem, but put the onus on PC manufacturers for not properly following Intel’s advice:
If the Intel MEBx default password was never changed, an unauthorized person with physical access to the system could manually provision Intel AMT via the Intel MEBx or with a USB key using the default password. If the system’s manufacturer has followed Intel’s recommendation to protect the Intel MEBx menu with the system BIOS password, this physical attack would be mitigated.
Sintonen said that all the laptop computers he had tested so far were vulnerable to the attack.
Listing image by Getty Images
https://arstechnica.com/?p=1243291

