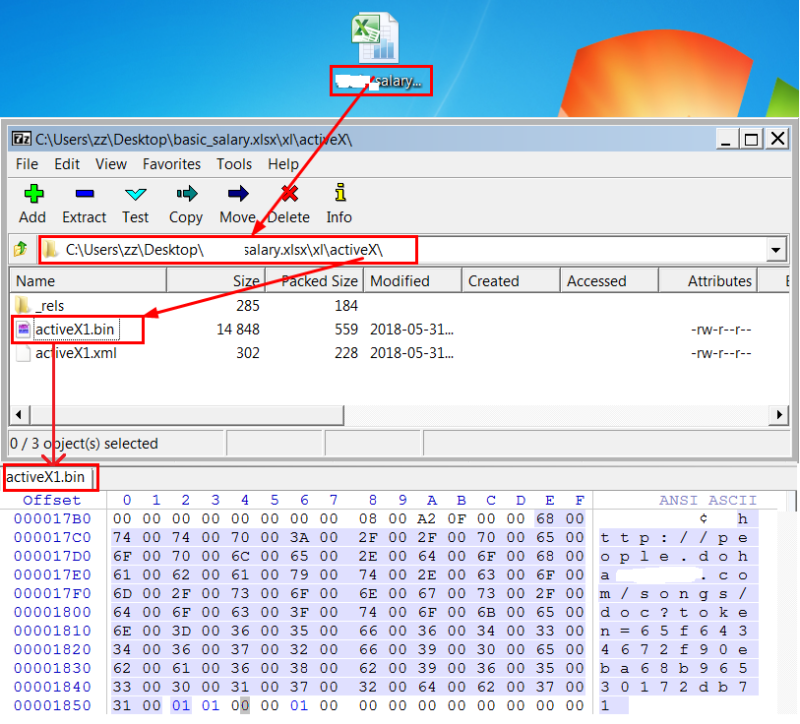
As browser makers make it increasingly hard to exploit vulnerabilities in Adobe Flash and other plugins, hackers targeting diplomats in the Middle East tried a new approach this month: using Microsoft Office to remotely load Flash content that used a potent zero-day flaw to take control of computers.
On Thursday, Adobe published a patch for the critical vulnerability, indexed as CVE-2018-5002. The stack-based buffer overflow was being triggered in an Office document that embedded a link to a Flash file stored on people.dohabayt.com. Once executed, the malicious file then downloaded a malicious payload from the same domain. That’s according to researchers from security firms Icebrg and Qihoo 360, which independently discovered the attacks and privately reported them to Adobe and wrote about it here and here.
Over the past few years, browser makers have begun to block Flash content by default, a change that has gone a long way to preventing drive-by attacks that exploit critical vulnerabilities in Adobe’s widely used media player. By contrast, at least some versions of Microsoft Office still download Flash with little or no user interaction, Icebrg CEO William Peteroy told Ars. To prevent downloads, users should ensure their installations prevent Flash from loading at all or at least don’t load Flash without explicit permission.
Read 7 remaining paragraphs | Comments
https://arstechnica.com/?p=1322989