
For years, malicious hackers have been hacking large fleets of MikroTik routers and conscripting them into Trickbot, one of the Internet’s most destructive botnets. Now, Microsoft has finally figured out why and how the routers are being put to use.
Trickbot came to light in 2016 as a trojan for stealing account passwords for use in bank fraud. Since then, Trickbot has mushroomed into one of the Internet’s most aggressive threat platforms, thanks to its highly modular, multistage malware framework that provides a full suite of tools that are used to install ransomware and other forms of malware from other hacking groups.
The malware driving Trickbot is notable for its advanced capabilities. It excels at gaining powerful administrator privileges, spreading rapidly from computer to computer in networks, and performing reconnaissance that identifies infected computers belonging to high-value targets. The malware often uses readily available software like Mimikatz or exploits like EternalBlue, which was stolen from the National Security Agency.
Hiding the C2
Trickbot operators, Microsoft said on Wednesday, are compromising MikroTik devices and using those devices to conceal the location of the command and control servers that exchange data and commands with infected computers. Instead of infected computers connecting directly to the control servers, the computers connect to the compromised routers, which act as go-betweens.
When security analysts monitor the connections infected computers make, the researchers see IP addresses belonging to compromised routers inside homes and businesses. The location of the control servers themselves remains hidden and can’t be detected without access to the proxy router. Here’s an overview:
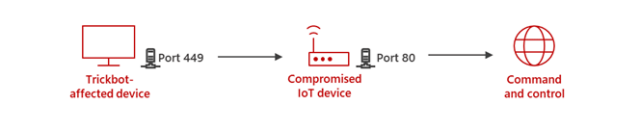
“The purpose of Trickbot using MikroTik devices is to create a line of communication between the Trickbot-affected device and the C2 server that standard defense systems in the network are not able to detect,” Microsoft researchers wrote. “The attackers begin by hacking into a MikroTik router.”
Microsoft said a chief reason Trickbot has such an affinity for MikroTik is MikroTik’s unique Linux-based RouterOS. This operating system allows users to remotely pipe commands that use the SSH, or secure shell, protocol. The flexibility and power of the commands make MikroTik routers an ideal proxy. Trickbot operators can send a single command that causes large numbers of the devices to funnel traffic in specific ways that are beneficial to the botnet architecture.
The commands, which are preceded by “/”, include things like /ip, /system, and /tool. They won’t normally work on regular Linux-based shell windows. MikroTik shells, by contrast, offer Trickbot operators a menu of useful options. For example, one command Microsoft observed Trickbot sending was:
/ip firewall nat add chain=dstnat proto=tcp dst-port=449 to-port=80 action=dst-nat to-addresses= dst-address=
That command creates a new rule, similar to iptables, that receives data from compromised computers through port 449. The command then redirects data through port 80 to command TrickBot servers.
“The said command is a legitimate network address translation (NAT) command that allows the NAT router to perform IP address rewriting,” Microsoft researchers explained. “In this case, it is being used for malicious activity. Trickbot is known for using ports 443 and 449, and we were able to verify that some target servers were identified as TrickBot C2 servers in the past.”
How to get owned, how to stay clean
Trickbot uses several methods to compromise the routers. Those methods include:
- Exploiting devices that still use default MikroTik passwords
- Performing password-guessing attacks, possibly using passcodes harvested from other MikroTik devices
- Exploiting CVE-2018-14847 on devices with RouterOS versions older than 6.42. This critical vulnerability gives the attacker the ability to read arbitrary files like user.dat, which contains passwords. Research from last year found that CVE-2018-14847 was one of three serious vulnerabilities found in 300,000 MikroTik routers.
Once the operators take control of a device, they change the password to prevent anyone else from remotely regaining control.
https://arstechnica.com/?p=1841904

