
A researcher has uncovered strange and unexpected behavior in Windows 10 that allows remote attackers to steal data stored on hard drives when a user opens a malicious file downloaded with the Edge browser.
The threat partially surfaced last week when a different researcher, John Page, reported what he called a flaw in Internet Explorer. Page claimed that when using the file manager to open a maliciously crafted MHT file, the browser uploaded one or more files to a remote server. According to Page, the vulnerability affected the most recent version of IE, version 11, running on Windows 7, Windows 10, and Windows Server 2012 R2 with all security updates installed. (It’s no longer clear whether any OS other than Windows 10 is affected, at least for some users. More about that in a moment.)
Below this paragraph in Page’s post was a video demonstration of the proof-of-concept exploit Page created. It shows a booby-trapped MHT file triggering an upload of the host computer’s system.ini file to a remote server. Page’s video shows the file being downloaded with Edge.
“This can allow remote attackers to potentially exfiltrate Local files and conduct remote reconnaissance on locally installed Program version information,” Page wrote. “Example, a request for ‘c:\Python27\NEWS.txt’ can return version information for that program.”
Beware of XML external entity attacks
Page’s demo is an example of an XML External Entity attack, wherein XML input is used to reference content stored on external sources. When the application parsing tainted XML doesn’t do so securely, it may disclose sensitive local information to the external entity.
Page released all the technical details and working exploit code after Microsoft told the researcher it was considering a fix but had closed the case and wouldn’t provide any status updates in the future. The vulnerability went largely unnoticed, most likely because IE has been deprecated and replaced with Edge, which by all accounts provides significantly improved security. What’s more, the two-click exploit (one click to download and another to run) requires some non-subtle social engineering of the target.
On Wednesday, security researcher Mitja Kolsek published a post warning that Microsoft had underestimated the severity of the vulnerability. The assessment was based on his discovery that Windows 10 users who open a malicious MHT file downloaded with Edge would also be attacked—and in a way that stole many more files than just the system.ini file in Page’s exploit. Even worse, Kolsek said, Page’s exploit could be improved to work more quietly and in a way that allowed the malicious file to be opened from Edge itself.
“This is clearly a significant security issue, especially since the attack can be further improved from what was originally demonstrated,” wrote Kolsek, who is CEO of ACROS Security and co-founder of “micropatching” service 0patch.
Enter mark-of-the-Web
Oddly, Kolsek said he couldn’t reproduce the attack when he used IE running on Windows 7 to download and then open the malicious file. While his process monitor showed that system.ini had been read, the file was never sent to the remote server.
“This looked like a classic “mark-of-the-Web” situation,” Kolsek wrote. “When a file is obtained from the Internet, well-behaved Windows applications like Web browsers and email clients add a mark to such [a] file in [the] form of an alternate data stream named Zone.Identifier, containing a line ZoneId=3. This allows other applications to know that the file has come from an untrusted source—and should thus be opened in a sandbox or an otherwise limited environment.”
The researcher confirmed that IE indeed put the mark-of-the-Web on the downloaded MHT file.
Kolsek then tried downloading the same file with Edge and opening it with IE, which remains the default application for MHT files. The exploit worked. After a large amount of analysis, he found the reason: Edge added two entries to the access control list:
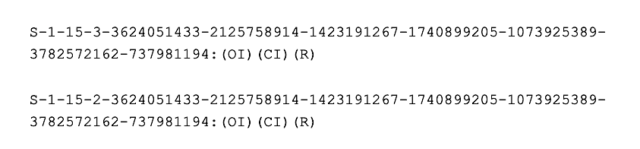
James Foreshaw of Google’s Project Zero vulnerability team said the entries Edge added are “capability and group SIDs for the Microsoft.MicrosoftEdge_8wekyb3d8bbwe package.” After removing the second entry—SID S-1-15-2-*—from the malicious file, the exploit no longer worked. Somehow, the permission Edge was adding allowed the file to bypass the sandbox in IE.
The question was—why? A great deal more analysis using a process monitor and IDA eventually showed that the permission prevented a function called GetZoneFromAlternateDataStreamEx from reading the file’s Zone.Identifier stream and returned an error. IE responded as if the file had no mark-of-the-Web and allowed the file to be sent to the remote server.
“See the irony here?” Kolsek wrote. “An undocumented security feature used by Edge neutralized an existing, undoubtedly much more important feature (mark-of-the-Web) in Internet Explorer.” (It’s arguable that the feature is documented here, but Kolsek disagrees.)
Despite the increased severity of Kolsek’s exploit and the new insights of his research, there’s no indication Microsoft intends to fix the bug soon, if at all.
“The technique described relies on social engineering and requires a user to download and open a malicious MHT file,” a Microsoft representative wrote in an email. “We encourage customers to practice safe computing habits online, including exercising caution when clicking on links, opening unknown files, or accepting file transfers. More information on staying safe online is available here.”
No doubt, the exploit is far from being a scary drive-by attack that takes full control of a computer. Still, in the right, ahem, edge cases, it might make the perfect exploit to use in targeted campaigns. Kolsek’s 0patch platform has published a micropatch that he says fixes the vulnerability.
This story was updated in the second and third paragraphs to remove incorrect details about Page’s PoC exploit.
https://arstechnica.com/?p=1493361

