
More than 100 e-commerce sites around the world are infected with malicious code designed to surreptitiously skim payment card data from visitors after they make purchases, researchers reported on Wednesday. Among those infected are US-based websites that sell dental equipment, baby merchandise, and mountain bikes.
In total, researchers with China-based Netlab 360 found 105 websites that executed card-skimming JavaScript hosted on the malicious domain magento-analytics[.]com. While the domain returns a 403 error to browsers that try to visit it, a host of magento-analytics[.]com URLs host code that’s designed to extract the name, number, expiration date, and CVV of payment cards that are used to make purchases. The e-commerce sites are infected when the attackers add links that cause the malicious JavaScript to be executed.
One of the infected sites identified by Netlab 360 is ilybean[.]com, an Orlando, Florida, business that sells baby beanies. As the screenshot below shows, the site executes JavaScript hosted at magento-analytics[.]com.
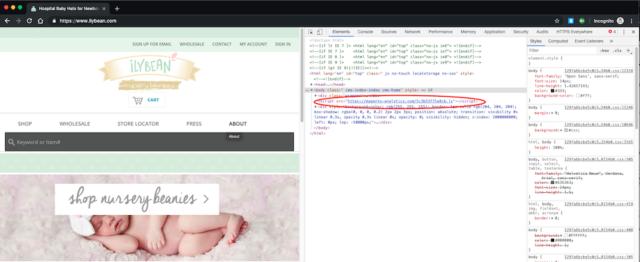
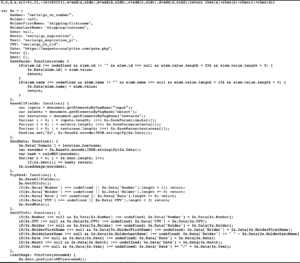
A quick review of the JavaScript, which is located at https://magento-analytics[.]com/5c3b53f75a8cb.js and partially shown to the right, shows a sprawling piece of code. While it’s hard for non-coders to fully parse, it includes tell-tale variable names, including verisign_cc_number, shipping:firstname, shipping:lastname, verisign_expiration, verisign_expiration_yr, and verisign_cc_cid. Functions suggest it collects the payment card data, and base 64 encodes it and siphons it away.
“This isn’t a new campaign, as the domain has been around for several months already, but it is one of the more active ones, according to our telemetry stats,” Jérôme Segura, head of threat intelligence at security provider Malwarebytes, told Ars. “We block an average of 100 connections to this domain daily from Malwarebytes users that visit an online store that’s been hacked.”
Segura pointed to this search query that showed 203 sites had been affected by the campaign. It appeared that some of the sites listed were no longer executing code hosted on magento-analytics[.]com, most likely because they had been disinfected after being indexed.
Most of the compromises reported by Netlab 360 appear to be hitting niche sites, but at least six of them are part of the Alexa top 1 million. They include:
- mitsosa[.]com
- alkoholeswiata[.]com
- spieltraum-shop[.]de
- ilybean[.]com
- mtbsale[.]com
- ucc-bd[.]com
Ars confirmed that all six of the sites were calling JavaScript hosted on magento-analytics[.]com at the time this post was being reported. Ars contacted each of the six sites to seek comment for this post but hadn’t received a response from any of them at the time this post was going live.
The compromises reported by Netlab 360 are part of a rash of infections that came to light starting late last year affecting, among others, sites for British Airways, Newegg, and seven other businesses with more than 500,000 collective visitors per month. In one case, a single site was infected by two skimming groups that competed against each other. The compromises were still going strong as of two months ago.
Historical IP and whois records show that magento-analytics[.]com has no relation to Magento, the e-commerce CMS that Adobe acquired last year. Attackers likely picked the name to confuse administrators of infected sites.
The full list of sites in Netlab 360’s report is:
adirectholdings[.]com
adm[.]sieger-trophaen[.]de
adventureequipment[.]com[.]au
alkoholeswiata[.]com
alphathermalsystems[.]com
ameta-anson[.]com
ametagroup[.]com
ametawest[.]com
appliancespareparts[.]com[.]au
armenianbread[.]com
autosportcompany[.]nl
bagboycompany[.]com
boardbookalbum[.]biz
boardbookalbum[.]com
boardbookalbum[.]net
boardbookalbums[.]biz
boardbookalbums[.]net
burmabibas[.]com
businesstravellerbags[.]com
clotures-electriques[.]fr
cltradingfl[.]com
colorsecretspro[.]com
connfab[.]com
cupidonlingerie[.]fr
devantsporttowels[.]com
diamondbladedealer[.]com
digital-2000[.]com
emersonstreetclothing[.]com
equalli[.]com
equalli[.]co[.]uk
equalli[.]de
eu[.]twoajewelry[.]com
eyeongate[.]net
fitnessmusic[.]com
fluttereyewear[.]com
freemypaws[.]info
gabelshop[.]ch
gosuworld[.]com
hotelcathedrale[.]be
huntsmanproducts[.]com[.]au
iconicpineapple[.]com
ilybean[.]com
imitsosa[.]com
jasonandpartners[.]com[.]au
jekoshop[.]com
jekoshop[.]de
junglefeveramerica[.]com
kermanigbakery[.]com
kermanigfoods[.]com
kings2[.]com
koalabi[.]com
lamajune[.]com
li375-244[.]members[.]linode[.]com
libertyboutique[.]com[.]au
lighteningcornhole[.]com
lighting-direct[.]com[.]au
lightingwill[.]com
liquorishonline[.]com
lojacristinacairo[.]com[.]br
magformers[.]com
maxqsupport[.]com
mdcpublishers[.]com
meizitangireland[.]com
mockberg[.]com
monsieurplus[.]com
mont[.]com[.]au
mtbsale[.]com
noirnyc[.]com
nyassabathandbody[.]com
pgmetalshop[.]com
pinkorchard[.]com
pizzaholic[.]net
powermusic[.]com
prestigeandfancy[.]com
prestigebag[.]com
prestigefancy[.]com
prestigepakinc[.]com
prettysalonusa[.]com
promusica[.]ie
qspproducts[.]com
qspproducts[.]nl
qspracewear[.]nl
rightwayhp[.]com
safarijewelry[.]com
schogini[.]biz
shopatsimba[.]com
spalventilator[.]nl
spieltraum-shop[.]de
storageshedsoutlet[.]com
stylishfashionusa[.]com
suitpack[.]co[.]uk
svpmobilesystems[.]com
task-tools[.]com
tiroler-kraeuterhof[.]at
tiroler-kraeuterhof[.]com
tiroler-kraeuterhof-naturkosmetik[.]com
ucc-bd[.]com
ussi-md[.]com
utvcover[.]com
vezabands[.]com
vitibox[.]co[.]uk
waltertool[.]info
waltertool[.]org
waltertools[.]com
workoutmusic[.]com
There’s no easy way for people to know for sure if an e-commerce site they’re browsing is infected. Malwarebytes and many other endpoint security programs will block the best-known campaigns, but new ones pop up so often that these products can’t be expected to catch all of them. People should never use debit cards when making online purchases. Credit card users should be sure to check their statements each month for fraudulent charges. People may also want to consider using temporary cards that have small, fixed lines of credit.
https://arstechnica.com/?p=1502017

