An alert released on Friday by the FBI and the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) revealed that the number of organizations targeted in a recent attack abusing a legitimate email marketing service was higher than initially reported.
Microsoft reported last week that the Russia-linked threat actor it tracks as Nobelium, which is believed to be responsible for the SolarWinds supply chain attack, had been abusing a legitimate mass email service named Constant Contact to target government and other types of organizations in the United States and a dozen other countries.
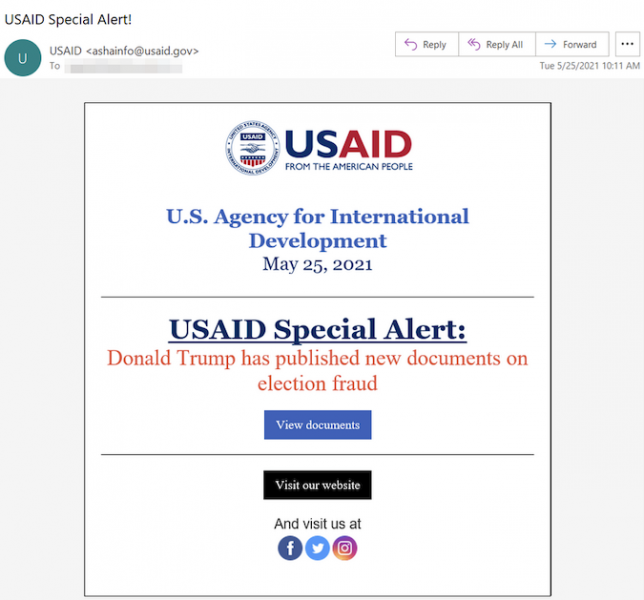
The attacks, which appear to have started on May 25, involved Nobelium compromising the Constant Contact account of the United States Agency for International Development (USAID), which is responsible for civilian foreign aid and development assistance. Microsoft said spear-phishing emails apparently coming from USAID and set up to deliver malware were sent to roughly 3,000 accounts across more than 150 organizations.
However, according to the FBI and CISA, the attackers actually sent spear-phishing emails to over 7,000 accounts at 350 organizations, including government, non-governmental and intergovernmental organizations.
Incident response firm Volexity, which has also seen the phishing emails sent out via Constant Contact, found some links to APT29, a well-known cyberspy group tied to Russia. In their joint alert, CISA and the FBI acknowledge the reports linking the USAID-themed attack to APT29, but the agencies say they have yet to attribute the campaign to any threat actor.
In their alert, the two agencies don’t mention the link to the SolarWinds attack and they don’t name the government agency being impersonated. They did note that the spoofed emails contained a legitimate Constant Contact link that redirected users to a malicious URL set up to serve a malicious ISO file containing malware and a decoy PDF document.
Microsoft noted that it had not seen “evidence of any significant number of compromised organizations at this time” and the White House reported that U.S. government agencies had largely fended off the attack.
CISA and the FBI have shared indicators of compromise (IOCs) that organizations can use to detect attacks. They also published a separate report focusing on the malware used in the attack.
In a second new blog post on Nobelium attacks, Microsoft described four pieces of malware used by the threat actor in recent operations, specifically EnvyScout, BoomBox, NativeZone, and VaporRage.
Microsoft also mentioned in its blog posts that Nobelium has exploited an iOS zero-day in some of its attacks. The vulnerability in question, tracked as CVE-2021-1879, was patched in March by Apple, which credited Google’s Threat Analysis Group for reporting it. Apple warned at the time that the “issue may have been actively exploited,” but no other details were made public.
In its latest blog posts on Nobelium, Microsoft also only provided limited information on the use of CVE-2021-1879.
“In one of the more targeted waves, no ISO payload was delivered, but additional profiling of the target device was performed by an actor-controlled web server after a user clicked the link. If the device targeted was an Apple iOS device, the user was redirected to another server under NOBELIUM control, where the since-patched zero-day exploit for CVE-2021-1879 was served,” Microsoft said.
Related: US Expels Russian Diplomats, Imposes Sanctions for Hacking
Related: SolarWinds Shares More Information on Cyberattack Impact, Initial Access Vector
http://feedproxy.google.com/~r/securityweek/~3/3Mkwyh5Mtjo/cisa-fbi-alert-350-organizations-targeted-attack-abusing-email-marketing-service



