Ransomware has become the most prevalent type of malware and it has increasingly targeted business-critical systems, according to Verizon’s 2018 Data Breach Investigations Report (DBIR).
The 11th edition of the DBIR is based on data provided to Verizon by 67 organizations, and it covers more than 53,000 incidents and over 2,200 breaches across 65 countries.
According to Verizon, ransomware was found in 39% of cases involving malware. Experts believe ransomware has become so prevalent due to the fact that it’s easy to deploy — even for less skilled cybercriminals — and the risks and costs associated with conducting an operation are relatively small for the attacker.
Cybercriminals have increasingly started using ransomware to target mission-critical systems, such as file servers and databases, which causes more damage to the targeted organization compared to only desktop systems getting compromised.
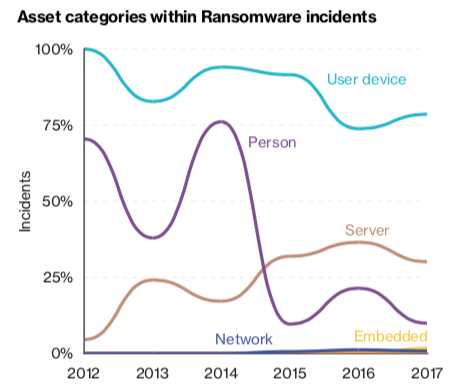
By targeting a larger number of devices and more important systems within an organization, attackers can demand bigger ransoms.
“What is interesting to us is that businesses are still not investing in appropriate security strategies to combat ransomware, meaning they end up with no option but to pay the ransom – the cybercriminal is the only winner here!” explained Bryan Sartin, executive director of security professional services at Verizon. “As an industry, we have to help our customers take a more proactive approach to their security. Helping them to understand the threats they face is the first step to putting in place solutions to protect themselves.”
According to the latest DBIR, financially-motivated attacks remain the most common and accounted for 76% of breaches analyzed in 2017. Cyber espionage is the second most common type of attack, accounting for 13% of breaches.
Nearly three-quarters of attacks were conducted by outsiders, half of which were organized crime groups, and 12% were state-sponsored threat actors.
Almost half of the attacks analyzed by Verizon involved hacking and 30% relied on malware. One in five incidents involved mistakes made by employees, including misconfigured web servers, emails sent to the wrong person, and failure to shred confidential documents.
While 78% of employees did not click on any phishing links, 4% will fall for any given campaign. This is a small percentage, but one victim is enough for an attacker to gain access to an organization’s systems, Verizon warned.
The telecoms giant also revealed that the number of incidents involving pretexting has increased more than five times since the previous DBIR. Of the 170 incidents analyzed in 2017, 88 targeted HR staff with the goal of obtaining personal data that could be used to file fraudulent tax returns.
Both an executive summary and the full report are available directly from Verizon in PDF format — no registration is required.
http://feedproxy.google.com/~r/Securityweek/~3/WSOYa6tYEoU/business-critical-systems-increasingly-hit-ransomware-verizon-2018-dbir



