Tel Aviv- and Boston-based CardinalOps has extended its detection posture management capability with MITRE ATT&CK Security Layers.
MITRE [email protected] has become the de facto standard source for measuring a company’s detection capabilities against primary attacks and attackers. ATT&CK contains more than 500 techniques and sub-techniques used by threat groups.
The principle is simple. If defenders can detect these techniques occurring in their networks, they can detect the presence of the attacker. But an effective realization is less simple given the quantity of ATT&CK techniques and the volume of alerts coming from detection systems.
CardinalOps’ working premise is that efficient and effective detection posture management against MITRE ATT&CK techniques can only be achieved with the help of automation. Its platform automatically measures detection rules used within SIEM/XDRs (including Splunk, Microsoft Sentinel, IBM QRadar, Google Chronicle SIEM, CrowdStrike Falcon LogScale, and Sumo Logic) against the techniques listed in ATT&CK. The process can improve the rule set while accurately measuring and allowing improvement to the detection posture.
The firm has now extended its platform with the addition of MITRE ATT&CK Security Layers. “Security Layers adds an additional dimension to ATT&CK coverage for the first time because it examines the ‘depth’ of coverage,” explains Phil Neray, VP of cyber defense strategy at CardinalOps.. Traditional ways of measuring MITRE ATT&CK coverage in SIEM/XDR platforms simply compile the number of detection rules for a given ATT&CK technique without considering the attack surface.
“Security Layers,” he continued, “enables you to implement ‘detection-in-depth’ by adding up the number of distinct security layers in your attack surface – endpoint, network, cloud, email, IAM, etcetera — that are covered for a given technique.”
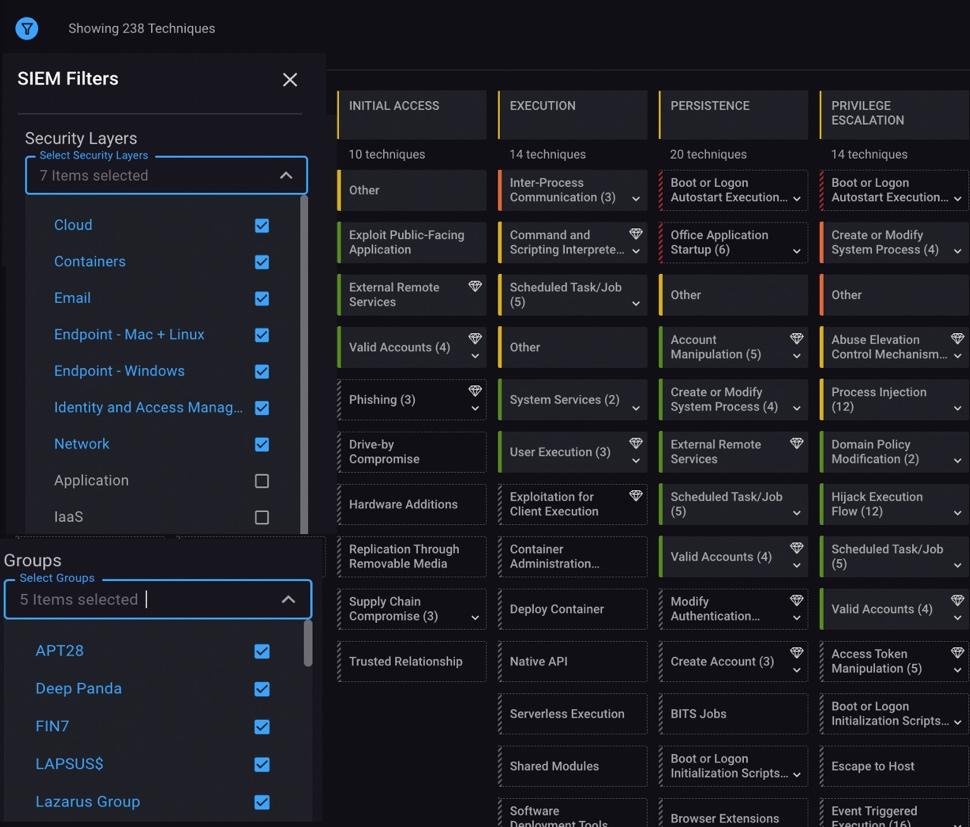
In the traditional approach, having five detection rules just for the endpoint layer counts the same as having five detection rules with each one covering a different layer. “Security teams,” added Neray, “want to know that they are covering multiple layers in their attack surface rather than bunching all their detection rules on just one or two layers like the endpoint and network layers, since this leads to gaps that attackers can exploit at other layers like cloud and IAM.”
Security Layers also allows defenders to link their coverage to preferred business outcomes by identifying blind spots related to crown-jewel assets such as their most sensitive applications and data. “For some companies like financial services firms,” he continued, “it can be their cloud assets, whereas for other companies such as law firms it might be their email systems. Security Layers enables organizations to proactively prioritize the development of new detection rules based on the crown jewel assets and the adversary techniques that are most important to them.”
The result, suggests CardinalOps, is the combination of a ‘detection-in-depth’ concept to the basic requirement for ‘defense-in-depth’ cybersecurity. “What’s new,” said Neray, “is the concept of looking for critical coverage gaps based on how many layers of your attack surface are not covered by existing detection rules.”
CardinalOps was founded in 2020 in Tel Aviv by Michael Mumcuoglu (CEO). The firm raised $17.5 million in a Series A funding round led by Viola Ventures in March 2022 – bringing the total raised to $24 million.
Related: MITRE Adds D3FEND Countermeasures to ATT&CK Framework
Related: CISA Issues MITRE ATT&CK Mapping Guide for Threat Intelligence Analysts
Related: ATT&CK v9 Introduces Containers, Google Workspace
CardinalOps Extends MITRE ATT&CK-based Detection Posture Management

