Exploit and vulnerability intelligence provider VulnCheck has issued a warning over fake security researcher accounts distributing malware disguised as zero-day exploits for popular software.
The campaign was discovered in early May, when VulnCheck came across a GitHub repository hosting code that its author claimed to be a zero-day for the Signal messaging application.
Throughout May, the cybersecurity firm continued finding such accounts on GitHub, offering what they claimed to be zero-day exploits for applications such as WhatsApp, Chrome, Discord, and Microsoft Exchange.
More recently, VulnCheck noticed that the campaign’s operator has also started creating Twitter accounts that appear to belong to security researchers and using them to lure people to GitHub repositories hosting the fake zero-day exploits.
The fake researcher accounts on Twitter have profile pictures — in some cases they are the photos of known researchers — and they claim to be associated with High Sierra Cyber Security, an entity that does not seem to exist.
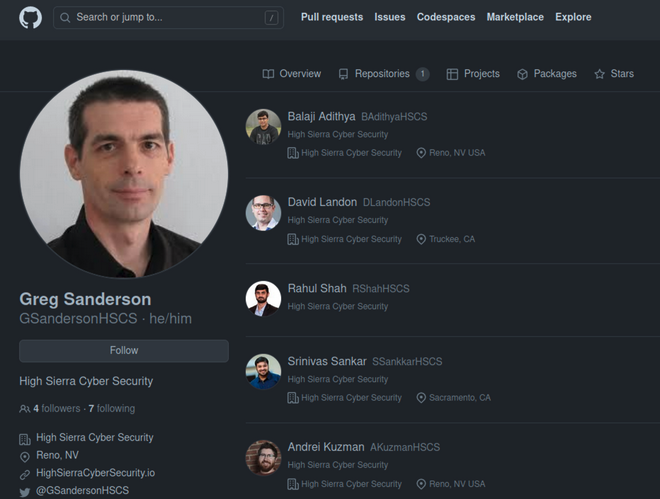
The code hosted in the GitHub repositories is designed to download a malicious binary and execute it. The downloaded binary can be a Windows or Linux file, depending on the victim’s operating system. A brief analysis of these binaries makes it obvious that they are malware.
“The attacker has made a lot of effort to create all these fake personas, only to deliver very obvious malware. It’s unclear if they have been successful, but given that they’ve continued to pursue this avenue of attacks, it seems they believe they will be successful,” VulnCheck said.
The GitHub accounts seen by VulnCheck have been suspended, but the fake Twitter accounts are still online at the time of writing.
It’s unclear if this is a campaign run by a threat actor or if it’s part of some sort of experiment, but the cybersecurity community has been advised to act with caution when executing code from untrusted sources.
Sophisticated threat actors targeting security researchers is not unheard of. In 2021, Google warned that North Korean hackers had delivered malware to security researchers after gaining their trust.
Research conducted recently by Leiden University showed that GitHub hosted hundreds of malicious repositories advertised as proof-of-concept (PoC) exploits.
Related: South American Cyberspies Impersonate Colombian Government in Recent Campaign
Related: Iranian APT Leaks Data From Saudi Arabia Government Under New Persona
Related: Python, JavaScript Developers Targeted With Fake Packages Delivering Ransomware
https://www.securityweek.com/fake-security-researcher-accounts-pushing-malware-disguised-as-zero-day-exploits/

