Nearly half a million Ubiquity devices may be affected by a vulnerability that has already been exploited in the wild, security experts warned last week.
Jim Troutman, consultant and director of the Northern New England Neutral Internet Exchange (NNENIX), revealed last week on Twitter that hackers had been remotely targeting Ubiquity networking devices exposed via a discovery service accessible on UDP port 10001.
Troutman said attackers had been launching denial-of-service (DoS) attacks that caused a device’s management features to become unavailable. He also warned that it’s possible to exploit the flaw for weak distributed DoS (DDoS) attacks.
The issue has been discussed on Ubiquity forums since at least last summer and Rapid7 has reported seeing traffic destined for port 10001 for more than a year. However, Ubiquity appears to have been aware of the weakness and it alerted users after Troutman’s warning on Twitter.
The vendor claims it has been working on a firmware update that should address the problem. In the meantime, it has advised users to block the problematic port at the network perimeter as a temporary workaround.
Interestingly, the company told customers that the flaw cannot be exploited to “create a DDoS attack.” It also told users that the vulnerability does not allow an attacker to gain control of devices.
However, Troutman, who says Ubiquity’s suggested workaround could disrupt some services, claims to have seen DDoS amplification attacks, but with a fairly small amplification rate (“56 bytes in, 206 bytes out”). He is also not convinced that it’s not possible to exploit the vulnerability to remotely hack devices.
Rapid7 researchers have also monitored these attacks and warned that the problematic service could have other management capabilities either “baked in or nearby.” As for the possibility of DDoS attacks, Rapid7’s Jon Hart noted in a blog post that UDP amplification vulnerabilities can typically allow attacks with an amplification rate that reaches up to 30-35X.
An Internet scan conducted using Rapid7’s Sonar project revealed roughly 490,000 unique devices accessible on UDP port 10001. More than half are located in Brazil, but significant numbers have also been identified in the United States, Spain and other countries.
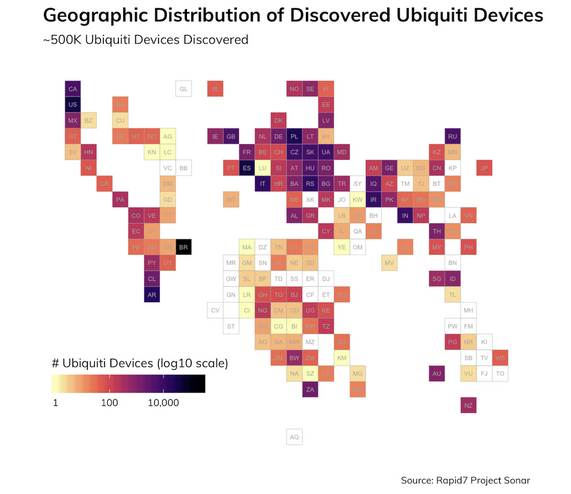
A majority of the exposed Ubiquity devices are NanoStation (172,000), AirGrid (131,000), LiteBeam (43,000), PowerBeam (40,000), and NanoBeam (21,000) products.
The names of 17,000 of these devices – they contain the string “HACKED-ROUTER-HELP-SOS” – suggest that they have already been hacked via other vulnerabilities. This is not surprising as Rapid7 claims most of the discovered devices are running outdated versions of the firmware.
Related: Worm Infects Many Ubiquiti Devices via Old Vulnerability
Related: Critical Flaw Exposes Many Ubiquiti Devices to Attacks
Related: Flaw Allows Hackers to Find Ubiquiti Devices Exposed to Web
http://feedproxy.google.com/~r/Securityweek/~3/-V8MQunxIIY/flaw-possibly-affecting-500000-ubiquity-devices-exploited-wild



