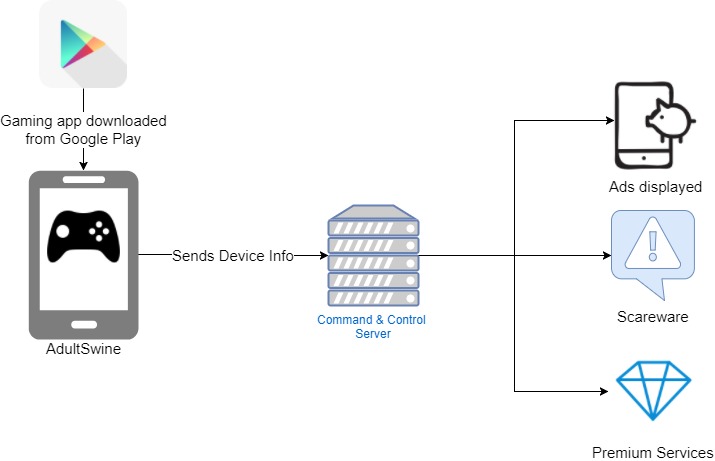
Sixty games were booted off the Play Store after security firm Check Point discovered that they contained pornographic ads and malicious components. Before their removal, the games were downloaded between 3 million and 7 million times, according to the download metrics on the Play Store.
The malware is dubbed “AdultSwine,” and according to Check Point Research, it had three main features:
- Displaying ads from the Web that are often highly inappropriate and pornographic
- Attempting to trick users into installing fake “security apps”
- Inducing users to register to premium services at the user’s expense
The 60 listings in the Play Store were generally knockoff games, like “Five Nights Survival Craft.” In some cases, the creator simply stole a real IP, as in “Drawing Lessons Angry Birds.” Once installed, the app would phone home, sending information about the user’s phone and receiving instructions on how to operate. The app could hide its icon, making removal more difficult. Check Point says the malware could display ads from “the main ad providers” or switch to its own ad server, which provided porn ads, scareware ads, and ads that tricked the user into signing up for premium services. AdultSwine not only displayed ads while users played the game that came with the malware; it could also show pop-up ads on top of other apps.
Google removed the apps once it was notified of them, telling the Financial Times, “We’ve removed the apps from Play, disabled the developers’ accounts, and will continue to show strong warnings to anyone that has installed them. We appreciate Check Point’s work to help keep users safe.” Google does automated malware scanning of apps submitted to the Play Store, leading to a continual cat-and-mouse game of malicious developers working to beat the filters in various ways.
https://arstechnica.com/?p=1243355

