Roughly one-third of the ICS-specific vulnerability advisories published in 2018 contained basic factual errors, including when describing and rating the severity of a flaw, according to the 2018 Year in Review report published on Thursday by industrial cybersecurity firm Dragos.
Last year, Dragos tracked 204 public advisories describing vulnerabilities impacting industrial control systems (ICS) and flaws in IT products that affect the safety of process control networks, including VPNs and firewalls. These advisories – an average of 17 advisories per month – covered 443 vulnerabilities. In comparison, the company tracked 163 advisories in 2017, with an average of 14 per month.
Of all the advisories it tracked, Dragos found that 32% had errors, particularly in terms of CVSS scores. Experts widely agree that CVSS scores can be misleading for ICS vulnerabilities, but it’s even more problematic if the CVSS score is not calculated properly.
“The overall high number of inaccurate reports is a risk – many organizations use public advisory data to either reduce risk or satisfy compliance requirements. Inaccurate advisories mean that these efforts are wasted and that relying upon advisories to prioritize patching or other remediation is not meeting the goal of reducing risk,” Dragos said in its report.
The company has pointed out that vulnerabilities reported through third-party vendors typically have a higher chance of getting an incorrect CVSS score assigned. When vendors find a vulnerability themselves and publish an advisory, the chances of an incorrect CVSS score are smaller – Dragos found that only 18% of vendor-produced advisories had errors.
It’s also better when researchers work directly with vendors as opposed to reporting their findings through a third-party agency such as ICS-CERT – 24% of advisories had errors when the flaw was reported directly to the vendor. Dragos noticed that 56% of the advisories published through an unnamed third-party organization had incorrect CVSS scores.
The security firm also determined that many advisories ignore industrial impact and fail to provide information on the likelihood of exploitation, which makes it more difficult for organizations to determine if the flaws require immediate action.
Learn More About ICS Flaws at SecurityWeek’s 2019 ICS Cyber Security Conference
The report also reveals that only 10% of advisories focus on perimeter systems that could be used by malicious actors to pivot into control system networks. On the other hand, 72% of the advisories cover vulnerabilities in HMIs, engineering workstations, field devices and industrial networking components.
Dragos believes researchers should focus more on products that could give attackers access to critical systems, such as VPNs, firewalls, data historians, OPC servers and other remote access systems. It highlighted that attackers who already have access to HMIs, field devices and engineering workstations can likely achieve their goals without the need to exploit any vulnerabilities.
Exploitation of ICS-related vulnerabilities can result in loss of view, when a system no longer displays data to the user or displays false data, and loss of control, when the system can no longer be controlled by the user.
More than half of the flaws disclosed last year can result in both loss of control and loss of view. However, 38% of advisories described issues that had another type of impact.
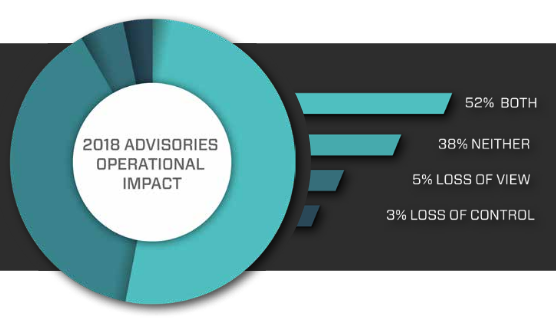
“Vulnerabilities which lead to both a loss of view and control occur in the core of traditional control networks affecting both field devices (PLCs, RTUs, etc.) as well as management devices such as human-machine interface (HMI) systems and engineering workstation (EWS) software. This means that over half (60%) of ICS-related vulnerabilities can cause an operations outage, at least for the component affected by the advisory,” Dragos explained.
In addition to its ICS vulnerabilities report, Dragos on Thursday published two other reports describing threat groups and the landscape, and lessons learned from threat hunting and incident response.
http://feedproxy.google.com/~r/Securityweek/~3/Y5VI1TNLKkQ/many-ics-vulnerability-advisories-contain-errors-report



