Microsoft is ditching the chemical elements in favor of weather-themed naming of APTs and other threat actors.
In a move designed to simplify the way APTs are publicly documented, Redmond said it would change the way advanced threat actors are named and will use weather events like Typhoon, Blizzard and Sleet to add better context to public APT disclosures.
Microsoft previously used an all-caps naming scheme linked to chemical elements like ACTINIUM and IRIDIUM to describe nation-state and other advanced malware tracking activity but now the company says the complexity, scale, and volume of threats demands a new naming taxonomy.
“With the new taxonomy, we intend to bring better context to customers and security researchers that are already confronted with an overwhelming amount of threat intelligence data,” said John Lambert, Corporate Vice President, Microsoft Threat Intelligence.
He said the new naming scheme will provide “a more organized, memorable, and easy way to reference adversary groups so that organizations can better prioritize threats and protect themselves.”
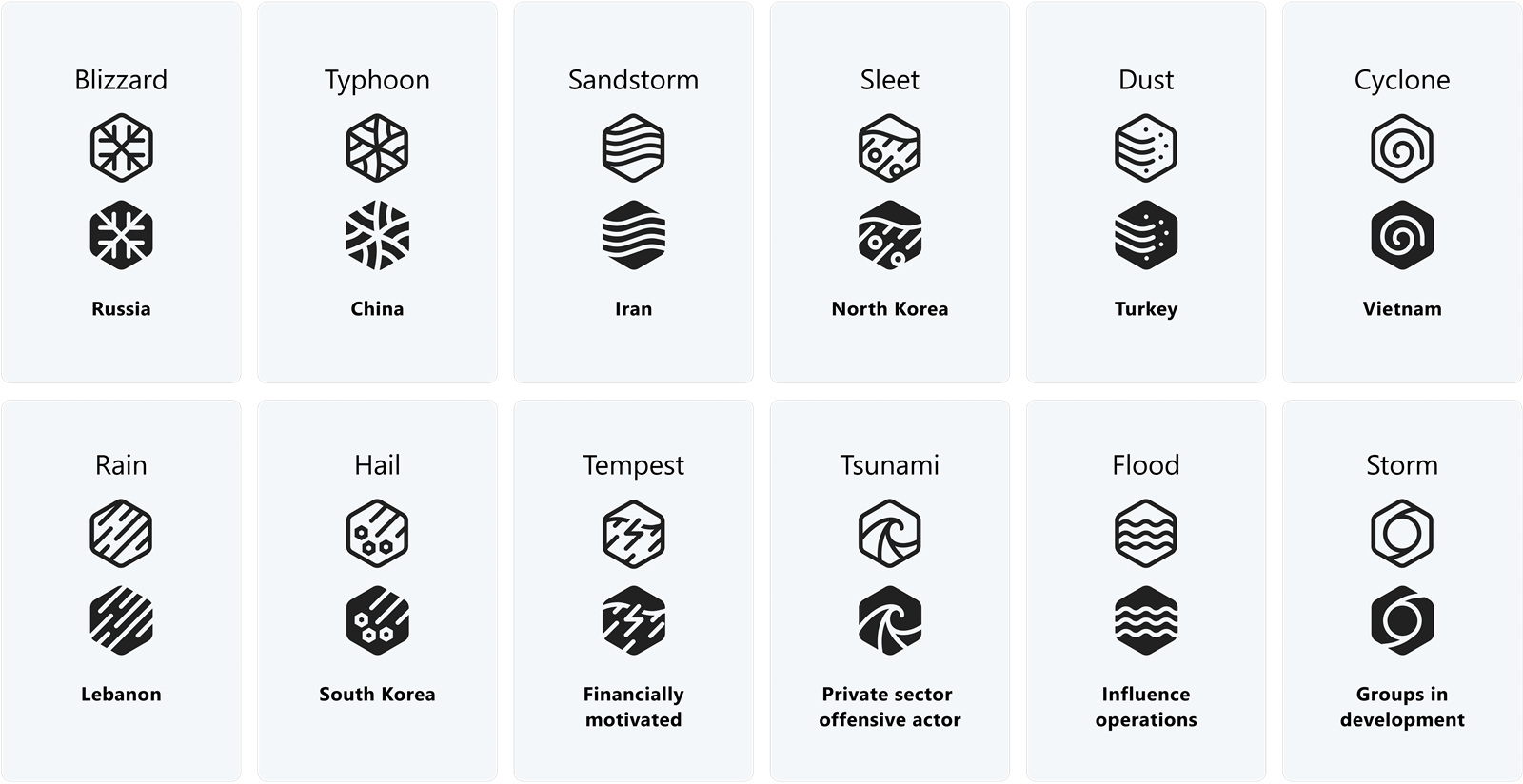
The new scheme will separate actors into categories — nation-state, financially motivated, private sector cyber-mercenaries, influence operations or groups in development — and pinpoint specific countries linked to malware operations.
“Simply put, security professionals will instantly have an idea of the type of threat actor they are up against, just by reading the name,” Lambert said.
This is how Microsoft plans to publicly track and identify nation-state malware activity:
| China | Typhoon |
| Iran | Sandstorm |
| Lebanon | Rain |
| North Korea | Sleet |
| Russia | Blizzard |
| South Korea | Hail |
| Turkey | Dust |
| Vietnam | Cyclone |
The company said financially motivated actors will be called Tempest while PSOA (private sector offensive actors) will be described as Tsunami.
Microsoft will name actors linked to influence operations as Flood and groups in development as Storm.
“We believe this new approach makes it even easier to identify and remember Microsoft’s threat actors,” the company said. To help threat intelligence and incident responders manage the transition, Microsoft published guidance that maps the older chemical element naming scheme to the new taxonomy.
Related: Microsoft Announces Disruption of Russian Espionage APT
Related: Microsoft Catches Austrian Company Exploiting Windows, Adobe Zero-Days
Related: Microsoft Spots Multiple Nation-State APTs Exploiting Log4j Flaw

