A researcher who specializes in hacking Apple’s iOS operating system has made public the details of an unpatched vulnerability in macOS that can be exploited to take complete control of a system.
The details of the exploit and proof-of-concept (PoC) code were made public on the first day of 2018 – or the last day of 2017, depending on where you are located in the world – by a researcher who uses the online moniker Siguza (s1guza). An attacker who has access to a system can leverage the vulnerability, which the expert has described as a “zero day,” to execute arbitrary code and obtain root permissions.
This local privilege escalation (LPE) vulnerability affects IOHIDFamily, a kernel extension designed for human interface devices (HID), such as a touchscreen or buttons. While trying to discover flaws that would let him hack the iOS kernel, Siguza noticed that some components of this extension, specifically IOHIDSystem, exist only on macOS, which led him to identify a potentially serious security hole.
The bugs he discovered affect all versions of macOS and they can lead to an arbitrary read/write vulnerability in the kernel. The exploit created by the hacker also disables the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI) security features.
However, the expert pointed out that his exploit, dubbed IOHIDeous, is not stealthy as it needs to force a logout of the logged-in user. On the other hand, an attacker could design an exploit that is triggered when the targeted device is manually shut down or rebooted.
Some of the PoC code made available by Siguza only works on macOS High Sierra 10.13.1 and earlier, but the researcher believes the exploit can be tweaked to work on the latest version as well, namely 10.13.2, which Apple released on December 6.
The expert believes the vulnerability has been around since at least 2002, but some clues suggest it could actually be a decade older than that. “One tiny, ugly bug. Fifteen years. Full system compromise,” Siguza said.
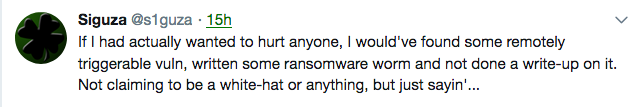
The researcher said he would have reported his findings to Apple instead of disclosing them to the public if the flaw had been remotely exploitable or if the tech giant’s bug bounty program covered macOS.
SecurityWeek has reached out to Apple for comment and will update this article if the company responds.
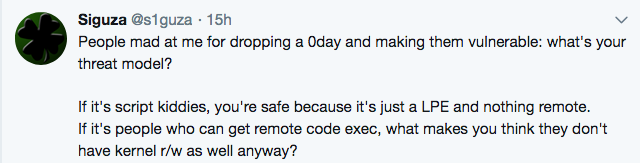
Some may argue that making the exploit public puts macOS users at risk of attacks, but Siguza believes that is not the case.
Related: Apple Patches Critical Root Access Flaw in macOS
Related: macOS Malware Spread Via Fake Symantec Blog
Related: Apple Silently Patched macOS Security Bypass Flaw
http://feedproxy.google.com/~r/Securityweek/~3/rrcvCaG6qCE/unpatched-macos-flaw-allows-code-execution-root-access



